In the last few months, I’ve seen an uptick in spoofed emails being sent with my own personal email domain. Not only is this extremely annoying, but more problematic is that recipients receive spam and phishing emails from what seems to be my personal mail account, simply by spoofing the from address. I don’t know why domain and email address has been “chosen” for this, but I guess this is fallout from the LinkedIn breach way back in 2012.
I didn’t think there was much I could do about this, but a recent tweet by my friend Per Thorsheim sent me down the rabbit hole.
I love my hard-fail SPF & DMARC email policy, and using @dmarcian to see how spammers fail to take advantage of my domain. :D
— Per Thorsheim (@thorsheim) April 12, 2017
Special offer for you my friend: Coffee & cake, and I'll show you HOWTO. :-D
— Per Thorsheim (@thorsheim) April 12, 2017
So, obviously there are options available to me that I was completely unaware of. I haven’t managed any public facing email services for 6-7 years, so I’ve not kept up with whatever has been happening in that particular space. Also, my personal email domain has been hosted by Google since 2008, so I haven’t really managed that either. Set and forget, right? Well, not quite.
So, what is this DMARC thing? It stands for Domain-based Message Authentication, Reporting & Conformance, and is a way to try and validate that emails from a given domain is being sent using one of the valid mail servers configured for that domain. In order to be able to use DMARC, you first need to first have Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) configured for you domain.
Here are the resources I used to get all of this configured for my domain:
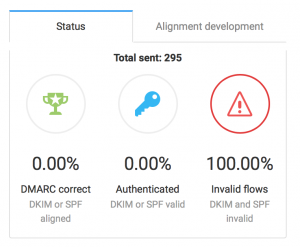
Since this file is a bit hard to read on it’s own, I uploaded it to DMARC Analyzer, and even though I knew a lot of email was being send with my email address as the reply to address, I was quite surprised to see that in less then 24 hours after I set up the DMARC DNS records, **a total of 295 emails had been rejected by mail servers all over the world, most of them sent from mail servers in Vietnam. **I_ do not_ send 295 emails a day with my personal email account, and absolutely none of them from Vietnam. In fact, during the time-frame of this initial aggregate report, I sent zero emails - as seen in the screenshot from the report.
I have now configured my DMARC DNS txt records to send emails directly to DMARC Analyzer, and I’m looking forward to seeing how these numbers add up over time. I’m currently on a free trial plan, and looking to evaluate which of the available DMARC Analyzers out there I want to use permanently.
At least now receiving email servers have a fighting chance of rejecting fake emails from my domain, since it’s now possible to verify that they are sent through a valid source.
Even if you don’t have problems with someone spoofing your email addresses, please spend 10 minutes configuring this for your domain as well. You never know when something like this might occur, and it’s better to build your defences before you get attacked. That way you stand a chance of stopping it before it gets as ugly as it did in my case.
And Per, you are a gentleman and a scholar. Even if I did manage to investigate and set this up on my own, cake and coffee is still on me!
