
As I’ve covered before, I run my home network mostly on Ubiquiti UniFi hardware. Since this offers a lot of nifty possibilities, I figured I should try to isolate all my “IoT”-devices in a separate network, while still making them accessible. After all, you don’t want a security issue on some sensor/automation thing you have in your house to be able to access and encrypt your familiy photos, right?
The thing that sits in the corner and controls the color of your lightbulbs, do not need to have access to the same network as your other data.
Right now, my list of devices looks like this:
- Amazon Echo(s)
- Google Chromecast and Google Home Mini
- Phillips Hue bridges
- Ikea Trådfri bridges
- Verisure Alarm System
Most of these are fine to just move into an isolated network, like the setup I’ve outlined previously, but not all of them. The Phillips Hue Bridge, IKEA Trådfri Gateway and the Verisure Gateway were all fine with being moved over to the new VLAN. This makes sense, as once they are configured all they do is communicate out to their respective cloud services — and the management apps for them connect to that service, not directly to the device itself.
The Amazon Echos and Google Chromecast/Home Mini is a different story though. This also makes sense, since these devices are supposed to receive data from your your other devices - directly. My primarily use case for them is Spotify Connect so I can stream music to my stereo setups (I have an old analog NAD receiver with some nice Dali speakers that do not have digital connections at all), so being able to actually stream music to them is rather useful.
The following information was correct at the time of posting, based on a setup with 1 x UniFi Security Gateway 3P (4.4.41.5193700), 1 x UniFi Switch 8 POE-60W (4.0.42.10433) and 5 x UniFi AP-AC-Mesh (4.0.42.10433)
1. Creating the Isolated IoT Network#
The process of creating, and isolating, a new IoT network is the same procedure as I have outlined before: Creating Isolated Networks with Ubiquiti UniFi.
Once you have this network in place, be it either via WiFi or via physical VLAN tagging on a switch port (or both), you can start moving your devices over.
The Phillips Hue Bridge, IKEA Trådfri Gateway and the Verisure Gateway was simple, since they are physically cabled, just move them over to a configured port on the UniFi Switch. These devices then got a new IP assigned to them from the new network definition, and their management apps still worked without problems.
1.2 Configuring the mDNS reflector#
For the Amazon Echos and Google Chromecast/Home Mini there are some other requirements that need to be in place. The first thing is to enable the Multicast DNS (mDNS) reflector. mDNS is a discovery protocol that enables discovery of the devices.
By default mDNS does not flow between VLANs, so in order to make discovery of these devices possible once they are in a separate VLAN, the Unifi mDNS Reflector needs to be enabled on the controller.
Log into your controller, and go to Settings->Services->MDNS and enable it.
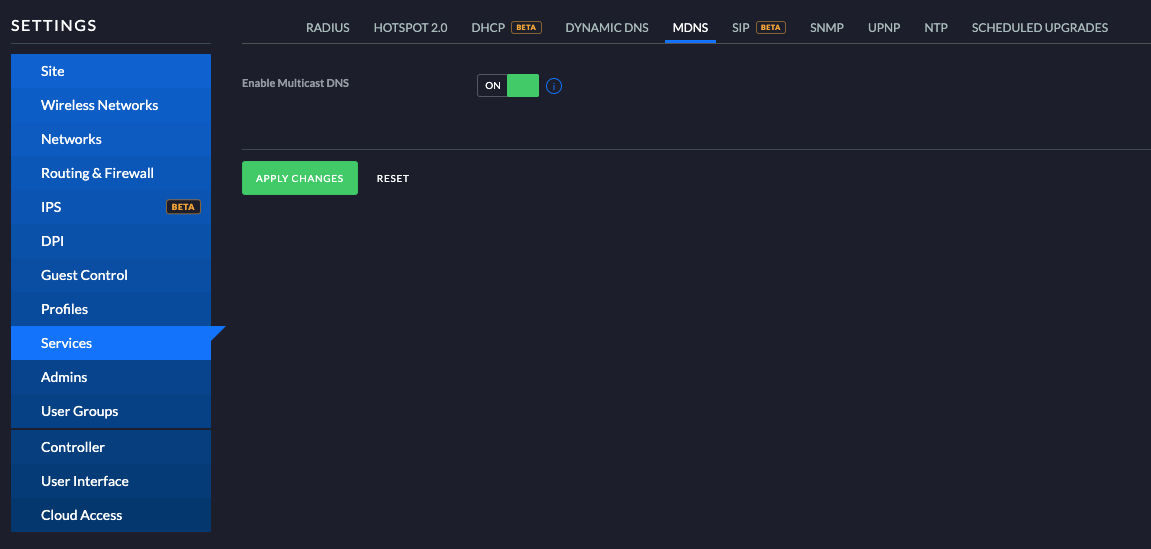
This enables mDNS requests to traverse the VLANs, and makes discovery across them possible.
1.4 Tweaking firewall rules#
The second thing that needs to be done, if it is not already in place, is to tweak the firewall rules between the IoT network and “normal” network. In the setup I’ve outlined previously, all traffic coming from the isolated network is blocked, and in order to be able to reach the Amazon Echos and Google Chromecast/Home devices properly, a new rule needs to be added.
Some traffic needs to be allowed back to the clients in the other VLAN, and the easiest way of doing this is by creating an allowed rule for Established and Related TCP/UDP states. In short, this means that connections that are already in place, or related to those established connections will be allowed.
This will still secure your networks, as devices in the IoT VLAN will still not be able to traverse the VLANs independently.
Give the rule a name that makes sense, enable it and expand Advanced. Find States and select Established and Related. Expand Sources, click on Network and select the “IoT” network you have created. Then go to Destination, select Network again, and choose the network your regular devices is located in.
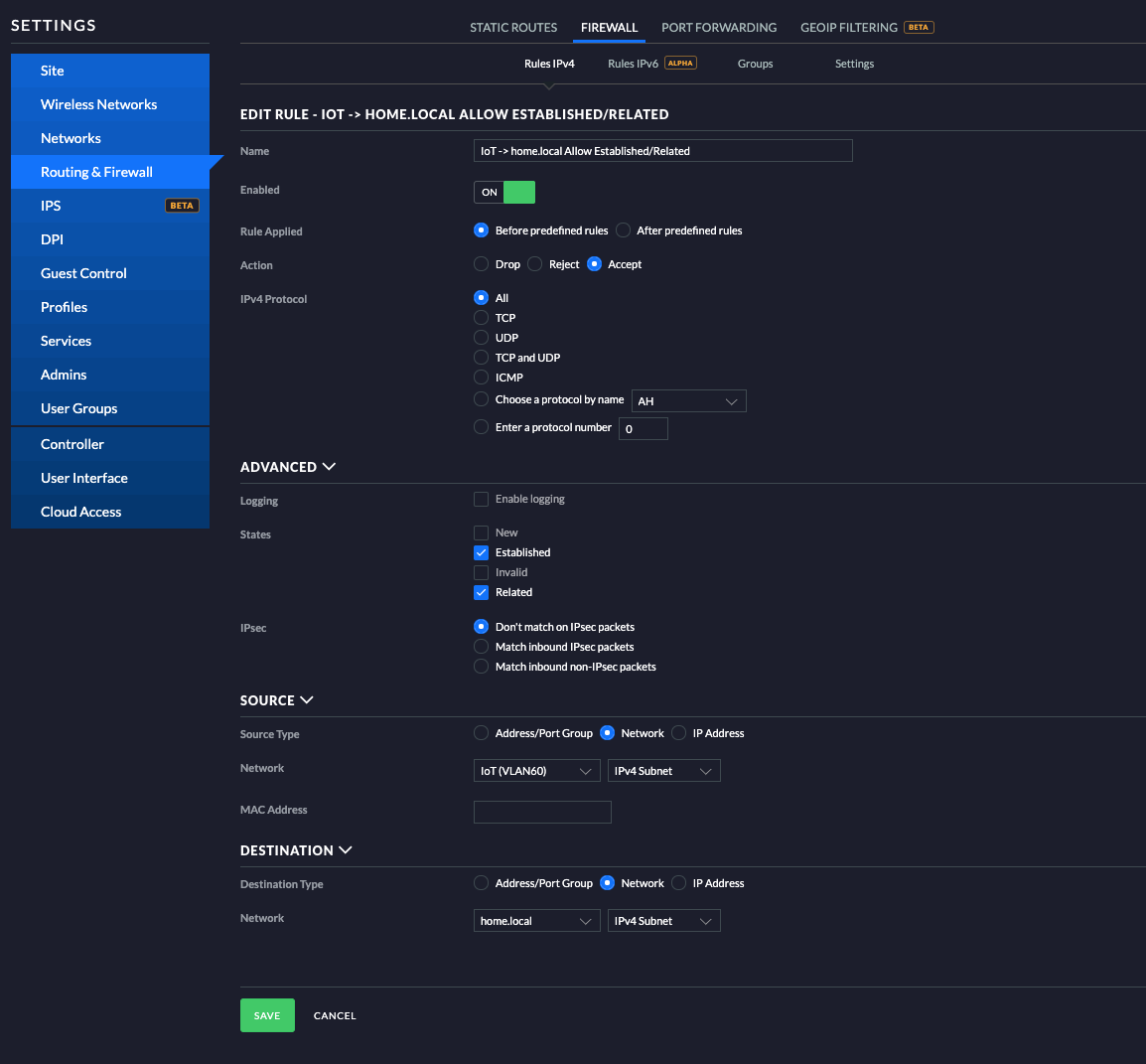
Click on Save to make the rule active.
1.5 Moving Wireless devices#
Now, you can start moving your streaming devices. Both Amazon Echo and Google Home Mini/Chromecast are easy to move to a new Wireless SSID.
For the Echo I just used the Alexa app on my phone, to move it over the new network — and the Google Home app did the same for the Google Home Mini and the Chromecast.
Screenshots#
Screenshots taken while connected to another SSID than the “IoT” network.
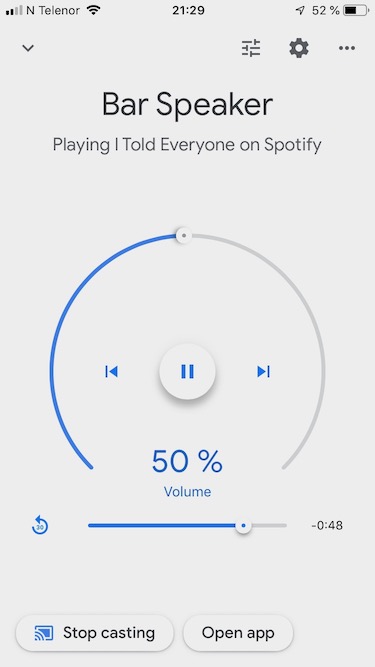
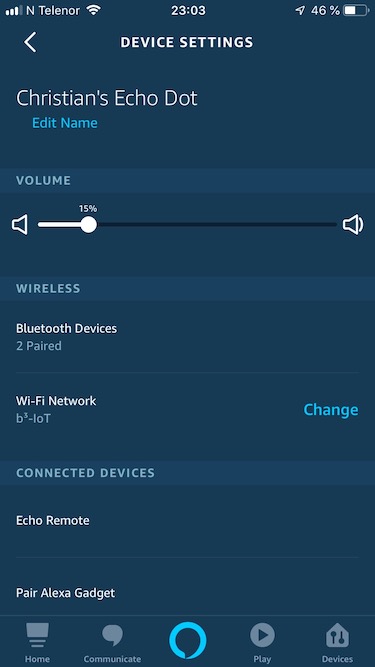
2 Specific Equipment#
2.1 Getting Sonos to work#
Updated September 9th 2019
Michael Ryom has come up with a recipe for enabling Sonos Wireless Speakers in a similar setup. In short, you’ll need to enable UPNP and open TCP/3500 in the firewall from the IoT Network, to your LAN. Check his tweet for screenshots.
Conclusion#
Once these steps are completed, streaming of data from your laptop/phone/tablet in the “normal” VLAN to the devices in your “IoT” network should still work as before, with the added security of not having them in the same network segment as the rest of your devices. I can still control my lights, and my alarm system, from my phone/tablet without any problems.
I do kind of like this.
